At the end of 2017, I’ve shared a post talking about Zabbix and Pure Storage monitoring. At this time we were using it as a POC. A few weeks later, we were so happy with the product that we decided to use it in production.
So it was an opportunity to rewrite my monitoring script from scratch.
It’s now time to share it with you.
If you want more information about the purpose, the way I’ve made the integration, etc. don’t hesitate to read my previous post as the only modifications are the code and the type of information the script can gather from the array.
Instead of writing a script for each part of the monitoring (volumes, array, disks,…), I’ve put everything in one file called “PureStorageMonitoring.py”.
The dependencies are still the same : purestorage and urllib3 libraries from Python and Python 3.x
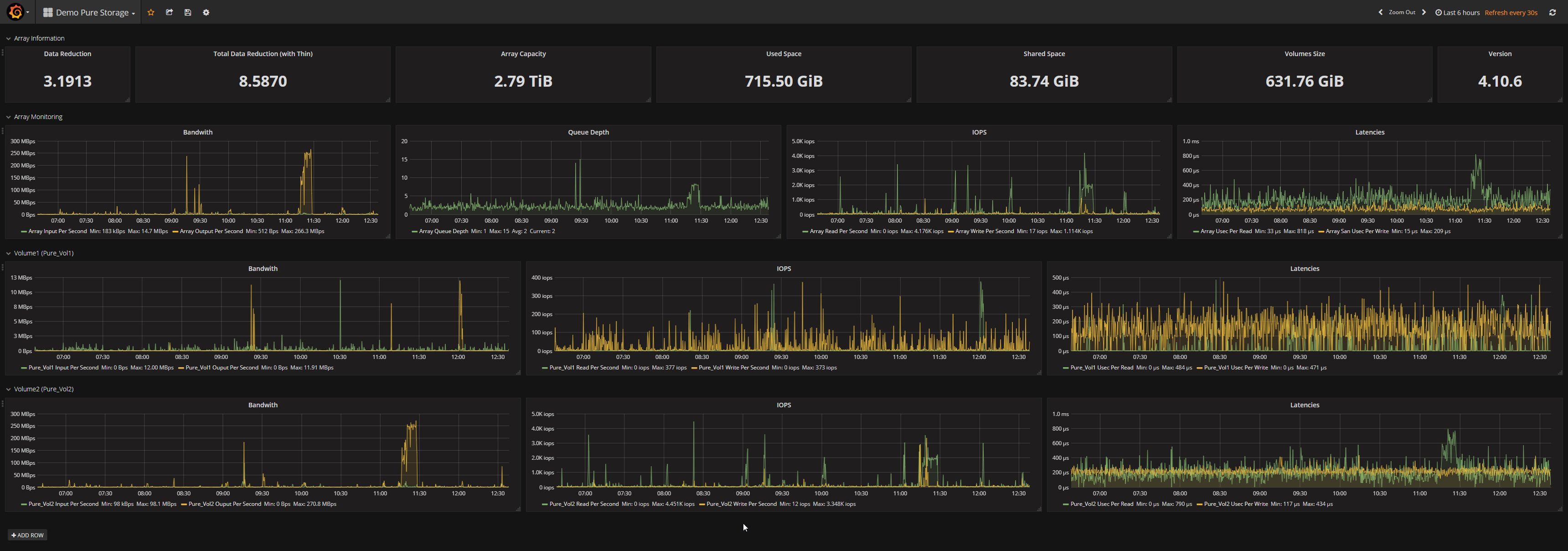
A complete list of datas and triggers that will be gathered by the script is available at the end of this post.
Important note : This script has been tested with Zabbix 3.4.x and 4.0.x and Pure Storage 4.10.x and 5.1.x. I cannot guarantee that it will work fine with any other version even if I made my best regarding this point. The template available is exported from Zabbix 4.0.x so you will have to delete some settings to import it in Zabbix 3.4.x don’t hesitate to contact me in case of trouble.
Setup the proxy or server
To gather data, we need to make some works on the Zabbix Proxy or Zabbix Server.
- Be sure that you have Python 3.x installed on the server
- Install the pip packages
pip3 install purestorage urllib3 py-zabbix
Get API Token
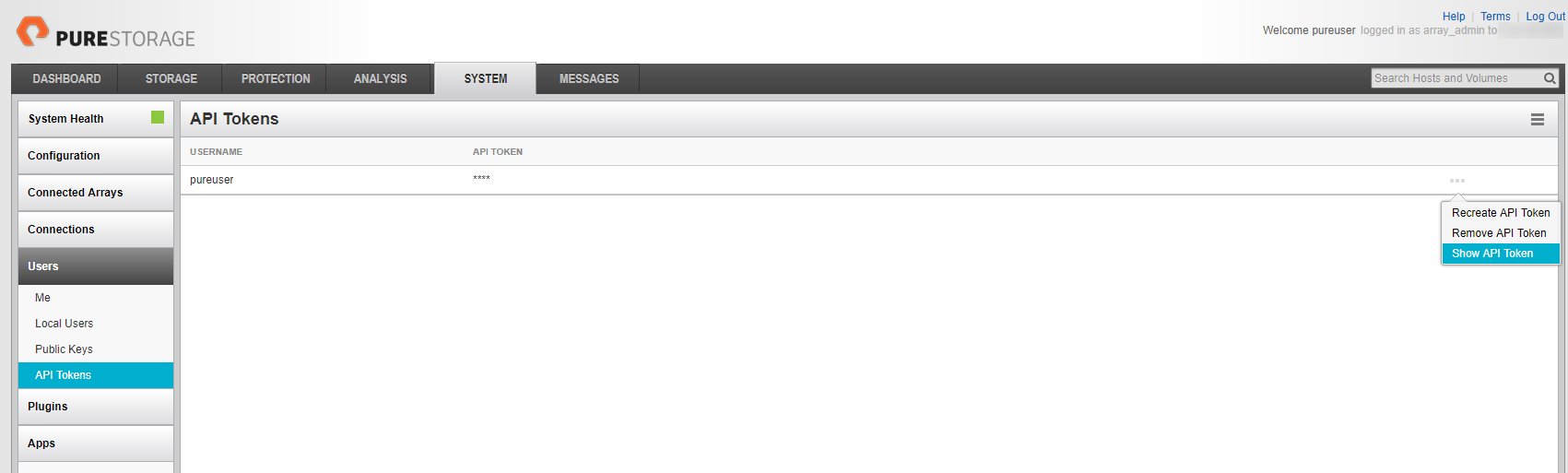
To be able to use the REST API of Pure Storage, you have to find your API Token on the web interface.
Go on “SYSTEM”, then “Users” and under the Users menu, you will find “API Tokens”. Click on the three dots on the right of the screens and use “Show API Token” to get your API Token.
Download the scripts
The script is available on my Github repository.
You can download it on the server using the following steps :
- Find the directory where you have to download it, by looking at the value of “ExternalScripts” setting of your proxy or server (by default it’s “/usr/local/share/zabbix/externalscripts” but if like me you are using the official Debian packages from Zabbix, it will be “/usr/lib/zabbix/externalscritps”
- Go to this directory
cd /usr/lib/zabbix/externalscripts
- Download the scripts
wget https://raw.githubusercontent.com/jeremyverda/zabbix-public/master/Pure%20Storage/PureStorageMonitoring.py
- Set the rights
chmod +x PureStorageMonitoring.py
chown zabbix:zabbix PureStorageMonitoring.py
Import the Zabbix template
You can find the Zabbix template on the Github repository.
You have to import it in Zabbix before you continue.
Configure the Zabbix host
In the Zabbix frontend, add a new host and set the information as follows :
- Agent interface IP : Fill in with the IP address of your Pure Storage
- Macros
- {$PURE_TOKEN_API} : Fill in with the API Token that you have copy previously
- {$PURE_ZBX} : WIll be the IP of your Zabbix Proxy or server that will be used by the Zabbix Sender. By default it will be 127.0.0.1
- Monitored by proxy : Set this field if you are going to use a Zabbix proxy
- Template : select the previously imported template : “Template Pure Storage”
Wait for the data
Once you have completed all the previous steps, you have to wait until the data are gathered by the script.
Data and triggers
Here is the list of data and triggers the script will gather from your Flash Array :
Data
- Global
- latencies
- read and write
- data reduction ratio
- array capacity, volume size, used space and shared space
- version
- remote assist
- phone home
- hostname
- etc.
- Volumes
- size and used size
- read and write
- latencies
- data reduction
- etc.
- Hosts (value corresponding to VMware or any other hosts connected to the array)
- latencies
- read and write
- Disks
- capacity
- last failure (currently this value won’t be empty but it will be corrected on a future API and Purity version)
- protocol
- status
- type
Triggers
- Global
- Phone home is disabled
- Remote assist is enabled
- Volume
- Volume size has changed
- Disks
- Error on disk status
This list will be updated for each data or trigger that will be added in the template. Don’t hesitate to ask me to add something if you need it.
Update
-
01/11/2018 :
- Replace the Zabbix Sender by a Python Library
- Increase the delay between each check
- Get more value at each check instead of requiring more check to get the same amount of values